Private equity (PE) firms hold the keys to the growth potential of numerous companies they own. With great power comes great responsibility, especially in the face of rapidly evolving cyber threats. Portfolio companies often possess valuable intellectual property, sensitive data, and critical operational systems that keep growing companies on target to meet their growth goals, making them juicy targets for cybercriminals. Their portfolio companies are also often in a combination of rapid high growth coupled with cost reduction efforts that often underfund cybersecurity and IT infrastructure investments that are necessary to establish a reasonable cyber defense. For PE firms, neglecting cybersecurity isn’t just irresponsible; it’s bad for business.
This article will cover common vulnerabilities, top threats, reasons why PE firms should enhance their focus on cyber, and some key actions for success.
How Risks Can Differ Depending on the Private Equity Company Type
PE firms and their companies being a target of cybercriminals have some parallels to the broader threat landscape that various service providers have faced over the last several years. CPA/accounting firms, IT-managed service providers, law firms, and PE firms are all central access points to large volumes of other companies, sensitive information, and the ability to pivot between companies through human deception or technology exploitation.
A company’s vulnerabilities typically stem from a lack of focus or gaps created by competing priorities that limit the focus on the efforts and controls that can minimize or mitigate the risk. Specifically for PE firms and the vulnerabilities of their portfolio companies, you can generalize the types of vulnerabilities of the various types of private equity investment. All PE firms want to grow a company and achieve an exit, which could be an IPO, or a sale to another PE firm, or a strategic buyer.
Venture Capital (VC): VCs are focused on early-stage startups and give a company a certain amount of seed funding in exchange for a share of ownership. At this early stage, the investments often haven’t turned a profit and have not significantly invested in infrastructure, as the business tactics can be fluid or under development. VC investments are typically high risk with a potential for a high reward if the company idea works. From a cybersecurity standpoint, the VCs aren’t always highly involved and may not prioritize cyber (especially with the fluidity of the early-stage growth.)
Growth Equity P.E.: Growth equity involves a capital investment in an established, growing company. Growth Equity PE firms get more into the details and the operations, customer success, and operational risks to make decisions to invest and protect their investment. At this stage of the portfolio company’s growth, they are scaling and investing in infrastructure and technology. From a cybersecurity standpoint, these types of PE investment firms are likely to be most focused or concerned about doing cybersecurity right. However, in all cases, it often comes down to the knowledge and quality of the PE firm and individual risk-taking and risk-management tactics.
Buyout or Leveraged Buyout (LBO): All PE firms are ultimately looking to achieve a buyout or exit. While an IPO is always an option if the company goes public, the exit could also be a buyout. The buyout could be to another P.E. firm or strategic investor (another company looking to broaden focus or customer base). Second or third-round PE firms are often going to be going deeper on scale and can often come with stronger risk management within cybersecurity.
A leveraged buyout occurs when a P.E. firm buys a company with a significant amount of borrowed funds. The assets of the company being acquired and the acquiring company are often used as collateral for the loans. These types of companies can have a bit of a reputation for being ruthless and time pressured, because of the leverage against both companies’ assets. From a cybersecurity standpoint, adequate investments are often skipped or minimized for a quicker turn on profit or an exit to cover the leverage.
Why are PE-owned companies vulnerable?
There are some specific reasons why PE-owned companies might be vulnerable as well as a desirable target for cyber criminals:
- Treasure Trove of Data: Imagine a treasure chest overflowing with financial records, business plans, proprietary information, and customer data. That’s essentially what a PE portfolio can look like to attackers. This data goldmine fuels competitive intelligence, extortion attempts, and identity theft.
- Immature Defenses: Many portfolio companies, especially emerging firms, lack the resources and expertise to build robust cybersecurity programs. This leaves them ill-equipped to defend against sophisticated attacks.
- Interconnected Networks: PE firms themselves act as bridges connecting multiple portfolio companies. A breach in one company can easily spill over to others, creating a domino effect of damage.
The Top 3 Cyber Threats for PE Owned Companies:
There are several key cyber threats that PE firms can face, and the list is probably not that surprising. These 3 take the cake in top risk across industries. However, there are some nuances for PE owned firms and the PE firms themselves within these 3 threat vectors.
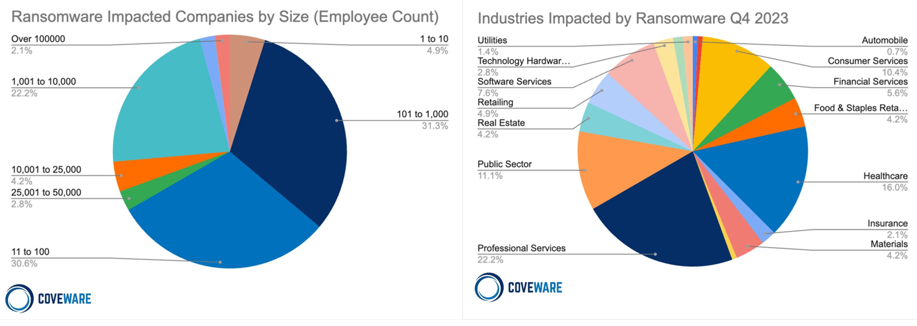
- Ransomware: This crippling attack encrypts critical data, holding it hostage until a ransom is paid. It can disrupt operations, damage reputation, and incur hefty financial losses. It is not surprising that ransomware is a top cyber threat to PE owned companies as the criminal tactic has plagued almost all industries. Coveware publishes a quarterly report on ransomware (see a couple figures from their most recent report). For PE firms and their portfolio companies, the key points are that smaller businesses are a huge percentage of the total ransomware impacted companies (30.6% with 11-100 employees and 31.3% having between 101-1000 employees. That spans ~62% of all cases. Secondly, professional services, healthcare, consumer services and the public sector are the most targeted industries. The PE company itself is a vector of professional services (investment and management), and as discussed earlier is a back door to their portfolio companies.
- Business Email Compromise (resulting in financial theft): Deceptive emails lure employees into clicking malicious links or sharing sensitive information, granting attackers access to systems and data. These emails are often masked to appear as a senior leader of the company asking for action. This is common in PE focused attacks because of what you might think, a PE firm is typically expected to carry heavy investor capital which is being deployed in helping the growth of the portfolio companies.
-
- PE Portfolio Company Example: Here is a recent example of a set of situations that happened to a PE portfolio company. They’ve done some of the basics, but funding got cut by the PE firm that owns them due to some unexpected business challenges. The organization shifted to “lights on” only focus and some focus on controls for critical system and other critical priorities friendly to limited capacity. Over time, the company has signed customer MSAs indicating they have cyber controls that they do not fully meet (in some cases, they don’t meet at all). Recently a large client from a regulated industry forced them to sign a new 3-year MSA (Master Services Agreement) with extensive cyber components with a legitimate concern their customer would leave for a competitor if they didn’t sign it and have the capabilities. The internal leadership re-made the case for funding and this time got the original funding requested. Unfortunately, that same week, they were hit with a six figure BEC (business email compromise) scam. This is not a unique story or example within this industry. At the end of the day, the total financial impact will be at least three times the cost of the original cyber priorities (including incident response, forensics, scrambling to do the priority cyber program items immediately, cost of the wire fraud/financial scam and other costs and non-tangible impacts.)
- Data Theft: Attackers steal valuable information like intellectual property, customer data, or financial records for their own gain or to sell on the dark web. All companies have something unique and/or innovative to provide. If they didn’t, they would have no competitive advantage or differentiators. If you have been savvy enough to attract PE money and be part of a strategic platform play (where the PE firm stitches together several companies to increase the value and offerings), than you can expect that someone outside the firm may stand to benefit from what you desire to secure within the company.
Investing in Security, Growing Value:
PE firms that prioritize cybersecurity can reap significant rewards with even modest investments in cybersecurity capabilities to protect their investment companies.
- Increased Deal Value: A strong cybersecurity program demonstrates due diligence and mitigates risk, making portfolio companies more attractive to potential buyers, leading to higher acquisition prices. I’ve participated in M&A deals on both side of the table and let’s just say that in this day and age, being able to show a future investment is protected can add equity to a deal. Ultimately, cyber security can be leveraged to provide enterprise value to a transaction.
- Favorable Negotiations: On the opposite end of the spectrum, companies without adequate cybersecurity measures lack leverage in acquisition negotiations. Investing in security allows PE firms to negotiate from a position of strength. If you are buying a company, finding poor cybersecurity can be like getting a horrible home inspection report when buying a new house. You bet you can ask for a lot of money to fix material gaps in the home which affects the final total closing price. The same holds true in M&A when evaluating cyber risk.
- Ensure compliance of customer contracts and Master Services Agreements (MSAs): The saying “read the fine print” could not be more fitting here as many fledging companies sign a lot of contracts with customers in high growth periods. When growth ambition outweighs readiness, a short sided decision to sign agreements making commitments of capabilities you don’t have can torpedo your ambitions. PE firms need to be better about evaluating, understanding and acting on these risks. PE owned companies need to do a better job fighting for appropriate funding and avoiding temptations to cut corners or “wish away” the risk.
Taking Action:
Both PE firms and companies owned by PE firms can become champions of cybersecurity by making some prioritized investments to understand risk, remediate gaps, and build a proactive posture to tell the story they want to tell for their likely exit as well as reduce risk to even getting to their exit. Some recommendations for moving to action include:
- Conducting Cyber Assessments: Identify vulnerabilities across portfolio companies and prioritize remediation efforts.
- Mandating Security Standards: Implement minimum cybersecurity requirements for all portfolio companies, ensuring baseline protection.
- Providing Resources and Training: Offer access to security expertise and training programs to empower portfolio companies.
- Promoting Cyber Insurance: Encourage portfolio companies to obtain cyber insurance to mitigate financial losses from breaches.
- Leading by Example: Implement robust cybersecurity practices within the PE firm itself, setting a positive example for portfolio companies.
I’ve seen far too many PE firms that pay for commodity check-box assessments to “feel good” vs truly addressing the challenges and opportunities covered in this article.
Cybersecurity is no longer an optional expense, it’s a strategic investment. The threats and the call to action is real and serious for both portfolio companies and the PE firms themselves. By prioritizing the cybersecurity and protection of their portfolio companies, PE firms can safeguard their investments, increase value, and contribute to a more secure and resilient corporate landscape. Remember, in the digital age, neglecting cybersecurity is like leaving the bank vault door wide open – an invitation for disaster and spoiling of growth aspirations. If you operate in this industry, I hope you choose to be the guardian, not the victim.
At Reveal Risk, we evaluate, design, and deliver strong processes and results in cyber, privacy, and risk that work efficiently, are fit-for-purpose, and are sustained. If you want assistance building your company’s cyber security strategy, governance, and plan towards desired state maturity, please don’t hesitate to contact us at info@revealrisk.com.
317.759.4453
About the Author
Aaron is a former Eli Lilly IT and security senior IT/Security/Audit/Privacy/Risk leader with over 20 years of experience in the pharmaceutical and life sciences sector. He founded the risk management working group for the H-ISAC (Healthcare Information Security and Analysis Center) which enabled information sharing and benchmarking across pharma, payers, and health care providers. Aaron is a certified Six Sigma blackbelt with career emphasis on building and improving internal processes and controls.