Protecting sensitive personal health information has been a regulatory requirement and a sensitive topic in the healthcare industry for decades. According to the FBI, cybercrime grew by 400% during the pandemic. Total losses since 2016 have topped $43 billion from Business Email Compromise. It was reported by the Threat Intelligence team at the Health-ISAC (Information Sharing and Analysis Center) in November 2023 that business email compromise in healthcare alone grew by 279% in 2022.
While money and personal health information loss are impactful in healthcare, the stakes have never been higher considering the potential for operational impairment of critical systems, life-saving medical equipment, and the operational ability of healthcare professionals to do their jobs. Doctors, nurses, surgeons, lab techs, and many other important roles that support the healthcare industry have remained in frontline critical jobs during the global pandemic and other health-related events. Physician practices, hospitals, clinics, nursing homes, youth and family services centers, and more have been challenged to catch up on defenses and continuity plans to remain resilient through a cyber attack.
Some common challenges are sustaining adequate focus, managing competing priorities, preventing staff burnout, and navigating confusion between compliance and cyber risk reduction. Elaboration on solutions around each of these challenges could be a full article individually. In this article, I will focus on cyber compliance vs risk reduction and how to avoid common pitfalls limiting that can limit organizations’ success in meeting their goals.
I observe a fair amount of industry confusion within healthcare between HIPAA compliance, aligning cyber cybersecurity programs to control frameworks, and navigating expectations when deciding between available options for external audits (including independent attestations and certifications).
My hope in this article is to provide some independent and unbiased information to:
- Help clarify any misnomers or misunderstandings leaders in your organization may have.
- Provide options for building/improving your cyber program that balances cyber risk and regulatory compliance.
- Share tips for finding and retaining an effective and credible audit partner.
At the end of the day, senior leaders within healthcare must strike the right balance between managing cyber risk, maintaining compliance, and allocating limited resources and budgets within their organization. Use the information here to help make the best decisions for your organization.
Clarifying Misnomers and Misunderstandings
Healthcare organizations are subject to various operational and privacy laws and regulations, with one very prominent one in the United States being HIPAA (Health Insurance Portability and Accountability Act). HIPAA is not a new regulation – and it is probably long overdue for a substantive update (the last major update was in 2013, with some new changes proposed in 2020 that are not yet effective). Do you remember what technology and computing was like in 2013? If you do, you know there have been many transformative technological changes over the last decade that the regulations haven’t kept pace with.
However, many of the principles around protecting data remain consistent, and even without it being fresh or new, some organizations still need help with the basics. Others have put the majority of their focus on compliance and are missing important elements that are exploited in today’s cyber threat landscape (especially ransomware).
It is reasonable to assume that US healthcare organizations will use HIPAA as a North Star for compliance and the set of minimum requirements from a technical and cybersecurity standpoint.
Let’s start with my Top 5 misnomers and misunderstandings in healthcare and HIPAA compliance.
- An organization can be certified in HIPAA: False. While there are some certifications for individual practitioners that focus on HIPAA compliance, there is no certification available for a company to obtain. Rather, there are various auditable frameworks to align your cybersecurity program’s control set to HIPAA requirements.
- “HIPPA” is a misspelling for a large hybrid aquatic/land-based animal, not the HIPAA you are looking for – it is shocking how much marketing content is out in the industry for solution providers purportedly solving compliance challenges that can’t seem to spell it. With all unfortunate but required jokes aside, HIPAA regulations remain very high level on technical requirements. Examples include:
- “Encryption: implement a system to encrypt ePHI when considered necessary.”
- “Integrity controls: implement security measures to prevent electronically transmitted ePHI from being improperly altered without detection until discarded.
- “Access controls: a covered entity must implement technical policies and procedures that allow only authorized persons to access electronically protected information.” While such flexible language allows laws to remain relevant as technology changes, it also creates space for confusion and competitive positioning of technical solutions that may or may not fully address compliance or cyber risk as claimed.
- HITRUST is required to be compliant with HIPAA: False. HITRUST is a framework that has been significantly adopted in healthcare. It entails independent certification (conducted by a certified 3rd party provider and certified by the HITRUST Alliance). Many organizations use the certification to demonstrate compliance with HIPAA requirements based on the standardized framework. HITRUST was created to provide an option for the healthcare sector to address information risk management across the complex ecosystem of companies and their 3rd party covered entities. The philosophy of HITRUST is to “assess once, report many,” – which means a consolidated control framework can be used for more than one purpose or requesting entity. It is important to note that HITRUST does not replace HIPAA compliance or prove the organization has attained or maintained compliance. However, it is widely accepted as a good approach for evaluating risk.
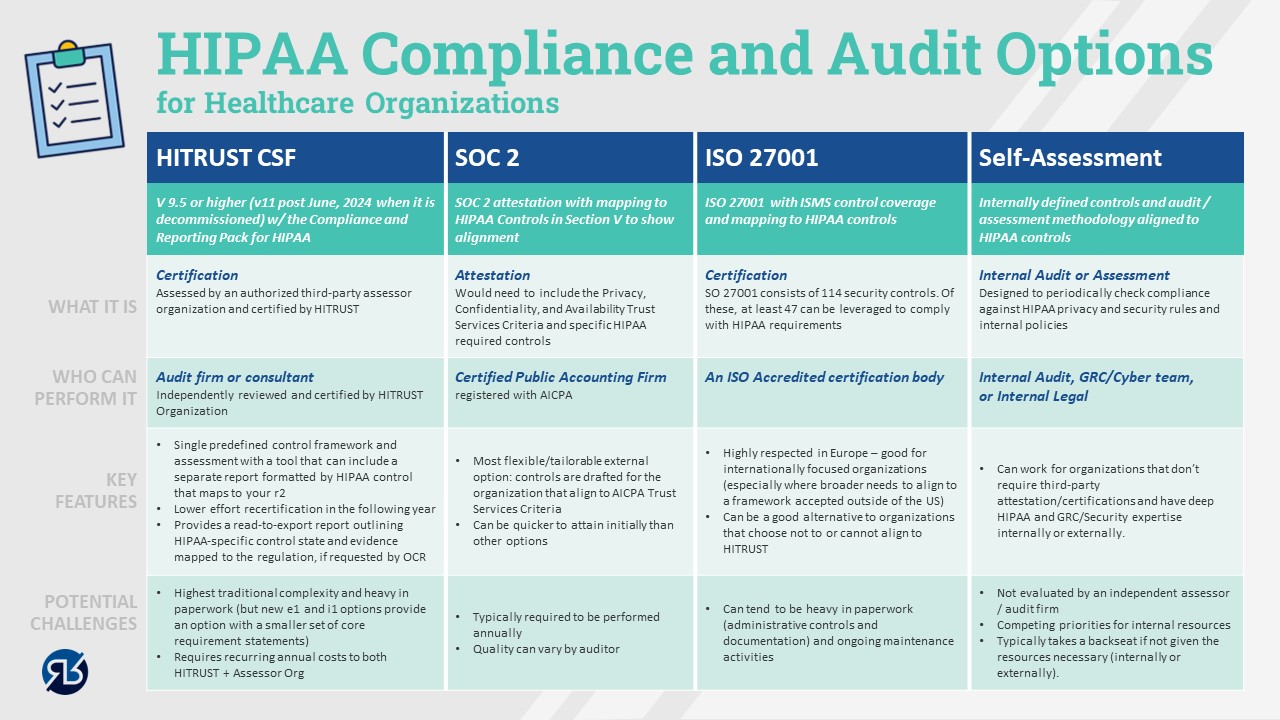
- Confusion about certification versus attestations and various external audit options that can support HIPAA risk and compliance management: This topic needs to be clarified. As I considered ways to reduce confusion, I remembered a picture is always worth 1000 words. The graphic below describes the landscape of options for both audit and compliance/cyber frameworks that can be leveraged.
- A purchased policy pack or software tool can ensure your readiness and compliance in a matter of weeks: It is a great claim, it just isn’t a realistic or accurate one for most organizations. If you are part of an organization that has bought a policy pack or SaaS solution that has promised an “out of the box” quick fix, you may have a good starting point, but likely have a long way to go. Like many things in life, finding easy buttons can be highly desired, but not always a reality.
Options for Building and Improving Your Cyber Program (balancing risk and compliance)
Many companies we talk to are starting at different levels of maturity. At the top end, we encounter large hospital systems that have a fully staffed and dedicated cyber program built on standard frameworks, with excellent defined policies, processes, and technology. These programs are continuously improving and helping to make both compliance and good cyber hygiene for healthcare workers easier and more integrated into productive workflows.
While that scenario is ideal, and we often are involved in helping to take that program to the next level, we more often see programs that are earlier in maturity. At the far other end of the spectrum, smaller entities or health systems often give responsibility to an employee who has other duties as well. Others fully outsourced cybersecurity to a managed security service provider, where approaches and results can vary drastically. We also have seen organizations that have made contractual commitments to customers and partners that compliance, data, and organizational protection controls are in place that do not actually exist. While the situations can be somewhat understandable in some situations, they can be a significant gamble that jeopardizes not only business relationships, but HHS OCR (Health and Human Services – Office for Civil Rights) enforcement ranging from $100 to $50,000 per violation plus criminal penalties and imprisonment for violations that are deemed to have been intentional.
Regardless of where your organizational maturity, there is hope. The biggest opportunity and challenge in healthcare cybersecurity is defining a clear strategy that balances cyber risk reduction and compliance needs. This strategy should establish a realistic and prioritized plan of action that ensures the most important and impactful decisions and initiatives are sanctioned first, so your cyber program is an asset that enables your operations instead of impairing them.
A common pitfall for developing cybersecurity programs is attempting to “boil the ocean,” doing too many things and trying to prevent every risk scenario. This is one reason why burnout in the field is so prevalent. This situation is very common, and we have come across some poor performing programs that have a seemingly unlimited budget. But when they have very little focus or are trying to accomplish too much, they, they often accomplish less than organizations that have much less funding.
A related failure mode we see occurs when leaders and teams over-buy cyber technology and tools, believing that these purchases will rapidly reduce risk. While there are some great tools in the market, they typically aren’t very effective when they have 10% adoption across the organization while the tech team is off procuring and implementing the next tool. One of the largest gaps in cyber programs that we see is focus on effective and efficient processes to enable people and technology to accomplish the intended risk reduction goals. “Cyber Process Engineer” should be a key position in all programs. If many organizations spent half as much money and time on this as they often do on cyber tools and procurement cycles, they might be surprised on how effective they would become.
I never loved the executive saying “do more with less” in the corporate world. It was typical rhetoric during cost-cutting exercises that did more to annoy than to motivate staff. However, I would get behind the phrase “Do more with what you have before you ask for the next thing.” A close cousin to that mantra would be: “Let’s see what we can get rid of before we add. What is not working/effective/adding value?”
Here are 6 key takeaways for building, improving, and maintaining an effective cybersecurity program in healthcare:
- Define a clear and realistic cyber program build/enhancement strategy, that aligns to budget reality and gets people focus and effective on what matters most to your business.
- Pick a maturity and controls framework that best aligns to your organization’s culture, risk needs, and compliance requirements.
- Engage your privacy, device, engineering, and/or clinical support teams to ensure your framework and controls address the unique challenges that healthcare devices, workflows, and compliance requirements entail.
- Define a realistic roadmap that phases work based upon impact, effort, and available internal and external talent.
- Enable a cyber governance process that proactively engages key business stakeholders and leadership. Be clear on what they own vs the CISO and how the mission only comes together if everyone knows their role and is held accountable to commitments and progress.
- Engage the workforce in compelling ways that stokes their hearts and minds to understand the importance of the work they do, and how their actions directly impact organizational success and protection of the patient’s data and lives.
Tips for Finding and Maintaining an Effective and Credible Audit Partner
Finally, the topic everyone has likely been on the edge of their seat for: picking their auditor! That sounds about as much fun as hoping for a “random” IRS tax audit selection or a three-hour follow-up visit to the dentist. With that said, if you are required have an audit conducted, who you entrust to help you on this journey can make a significant difference on how much pain your team endures. And the “right” answer isn’t the auditor that is the “easiest” or turns their head to avoid surfacing a complex issue. At the end of the day, you want to work with someone that is efficient, effective, transparent, and helps you work through issues promptly and without prejudice.
Top Considerations For Making an Audit Partner Selection
- Seeks to understand your business context and value of the audit solutions being proposed. As discussed in this article, there are many options to meet compliance and risk management goals. One size does not fit all. You should search for an audit partner that advocates for simplicity and minimal duplication (vs upsells to numerous audit expansions)
- Finds an appropriate balance but favors quality over low cost. Spend the extra time to validate the audit process, audit team acumen, and approach for interactions and testing with your team. Think about the total cost impact of the process, audit, and controls structure on your team. Cheap audits are often very expensive when you consider the churn and productivity lost to a poorly managed audit.
- Holds appropriate certifications and training for audit domains that you desire. In most cases (HITRUST, SOC 2, ISO), credentials or certifications (at the company and individual auditor level) are required to be able to provide such services. However, the level and depth of knowledge and investment can vary accords firms.
- Provides compelling references. This is a very important decision and you and your auditor should plan for a long-term professional relationship. Ask your potential auditor for client references and use that time to get unbiased feedback.
Top Warning Signs That You May Need A Change in Audit Partners
- Is your auditor double-dipping? (E.g., program building and auditing) Most large US-based consulting firms are diligent about excluding themselves from hands-on program-building work or advisory that could be perceived as helping to make “management decisions.” However, examples exist in the industry where some games can be played, and loopholes can be threaded to create a perception of independence. Some common loophole tactics involve separate LLCs with the same management/ownership. Additionally, some double-dipping firms may find an opportunity to do both audit and consulting for different divisions of your company – especially if they are incorporated as separate companies or affiliates. Even if it is legally permissible, the question of auditor independence is a key reason why the regulations and separation of services exist in the first place.
- Is your auditor rotating resources so frequently that context is lost, and redundant sessions or tests are necessary? Every team is bound to have some attrition. Individuals get promoted or move on to new opportunities. However, how much resource churn is too much? It really comes down to how transitions of resources on your account are managed. If staff swaps cost your team cycles or cause rework and confusion, the audit firm is probably not managing its staff rotations well.
- Is your auditor reasonable? You shouldn’t expect an auditor that will roll over on any pushback related to issues. If they did, they wouldn’t be credible. However, as with any relationship, mistakes and misunderstandings can happen. It may be time for a change if your auditor has not worked to build a good partnership and trust with you to work through such issues.
- Is your auditor transparent? Most audits shouldn’t include a lot of surprises. In most of the frameworks and audit types discussed in this article, the “answer key to the test” is provided. No one needs or deserves a “gotcha” auditor.
Hopefully, this has helped simplify the complexities of cybersecurity, compliance, and audits within the healthcare organization. If you have any questions or would like to have further conversations about the topics in this article, please reach out.
At Reveal Risk, we evaluate, design, and deliver strong processes and results in cyber, privacy, and risk that work efficiently, are fit-for-purpose, and are sustained. If you want assistance building your company’s cyber security strategy, governance, and plan towards desired state maturity, please don’t hesitate to contact us at info@revealrisk.com.
317.759.4453
About the Author
Aaron is a former Eli Lilly IT and security senior IT/Security/Audit/Privacy/Risk leader with over 20 years of experience in the pharmaceutical and life sciences sector. He founded the risk management working group for the H-ISAC (Healthcare Information Security and Analysis Center) which enabled information sharing and benchmarking across pharma, payers, and health care providers. Aaron is a certified Six Sigma blackbelt with career emphasis on building and improving internal processes and controls.



